Let’s dive into the intriguing world of Personally Identifiable Information (PII). You might have heard about it in the context of data security, but let’s unravel the enigma and take a look at what it truly means.
What is PII?
PII is like the golden nugget of data that everyone desires, from cyber criminals to corporations and even those elusive hackers. It’s all about personal data that can single you out, either on its own or when cleverly combined with other private details.
Imagine your full name, medical history, credit card details, social security number, and even your passport number—all this precious data falls under the umbrella of PII. It’s valuable and sought after like treasure buried deep in the digital realm.
The Two Faces of PII: Direct Identifiers and Quasi-Identifiers
Now, let’s shed some light on the two faces of PII:
- Direct identifiers
- Quasi-identifiers
Direct identifiers are like the master key to your identity. They can uniquely pinpoint you amidst the vast sea of data. But wait, it doesn’t stop there! Quasi-identifiers might not be as unique, but when they join forces with others, they can still reveal your hidden secrets. Let’s make a couple of examples:
Examples of direct identifiers as PII
Direct identifiers are specific pieces of information that, on their own, can directly identify an individual. Here are some examples of direct identifiers considered as Personally Identifiable Information (PII):
- Full Name: A person’s complete name, including their first name, middle name (if applicable), and last name, is a clear direct identifier.
- National Identification Numbers: National identification numbers or social security numbers, which are unique identifiers assigned to individuals by governments, fall under direct identifiers.
- Email Address: An individual’s personal email address is considered PII as it allows direct communication and is often linked to their identity.
- Phone Number: Personal phone numbers, whether mobile or landline, are direct identifiers as they directly relate to the individual.
- Home Address: A residential address, including street name, house number, city, and postal code, is a direct identifier as it points to a specific person’s location.
Examples of quasi-identifiers as PII
Let’s consider another example with five quasi-identifiers from an online survey:
- ZIP Code: The survey collects the ZIP code of respondents, providing a general geographic location.
- Education Level: Participants are asked about their highest level of education, such as high school, bachelor’s degree, master’s degree, etc.
- Ethnicity: Respondents are asked to identify their ethnic background, like Asian, African American, Caucasian, etc.
- Job Title: The survey includes a question about the job title or position of the participants.
- Marital Status: Participants are asked whether they are single, married, divorced, etc.
Individually, each of these quasi-identifiers might not reveal a specific person’s identity. However, when combined, they can create a more distinctive profile that may uniquely identify an individual.
For example, if a survey respondent is from a specific ZIP code, has a master’s degree, is of a particular ethnicity, holds a unique job title, and is married, this combination of quasi-identifiers could be rare enough to identify that person within a smaller group.
If such a combination of quasi-identifiers allows for the identification of an individual, either directly or indirectly, it would be considered as PII and subject to the regulation’s protection and handling requirements.
PII and metadata
Metadata, such as location data collected by a mobile app can also be considered PII and be used to infer or deduce the identity or attributes of a person, either by combining it with other data sources or by applying sophisticated algorithms and techniques.
For example, metadata such as the websites visited, the search queries entered, the products purchased, and the social media contacts of a person can reveal their preferences, interests, opinions, beliefs, habits, and relationships. Metadata can also be used to track and profile individuals and to influence their behaviour and decisions.
How to safeguard your PII
It is important to protect your PII from unauthorized access. You can do this by following some best practices, such as:
- Only provide your PII to trusted and legitimate websites or entities that have a clear and transparent privacy policy.
- Use strong and unique passwords for your online accounts and enable multi-factor authentication whenever possible.
- Avoid clicking on suspicious links or opening attachments from unknown sources that may contain malware or phishing attempts.
- Use encryption, VPNs, or other tools to secure your data when using public Wi-Fi or unsecured networks.
- Review your privacy settings and opt out of unnecessary data collection or sharing by online platforms or services.
- Monitor your credit reports and bank statements regularly for any signs of identity theft or fraud.
By taking these steps, you can reduce the chances of your PII being compromised and safeguard your online privacy and security.
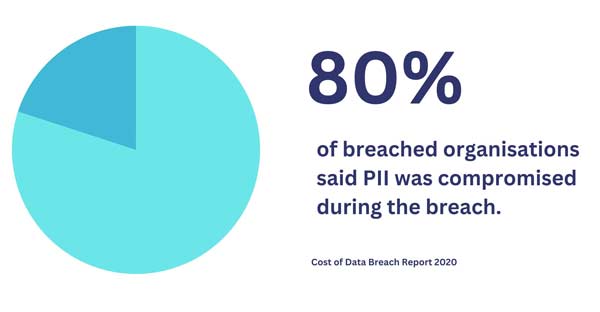
What if my PII has been compromised in a data breach?
If you learn that your PII has been compromised in a data breach, you should take immediate action to minimize the potential damage. Some of the steps you can take are:
- Contact the organization that suffered the breach and ask for more information about the incident and what they are doing to protect your data.
- Change your passwords and security questions for any affected accounts and any other accounts that use the same credentials.
- Freeze your credit reports with the three major credit bureaus (Equifax, Experian, and TransUnion) to prevent new accounts from being opened in your name without your permission.
- Check your credit reports for any suspicious activity or inquiries and report any errors or fraud to the credit bureaus and the Federal Trade Commission (FTC).
- Sign up for identity theft protection services that offer monitoring, alerts, recovery assistance, and insurance in case of identity theft.
- File a police report if you suspect that your PII has been used for criminal purposes.
By taking these steps, you can reduce the impact of a data breach on your privacy and security and restore your identity as soon as possible.